Trezor Login Token Approvals | How Trezor Login Manages Token Permissions | Trezor Login Token Approval System
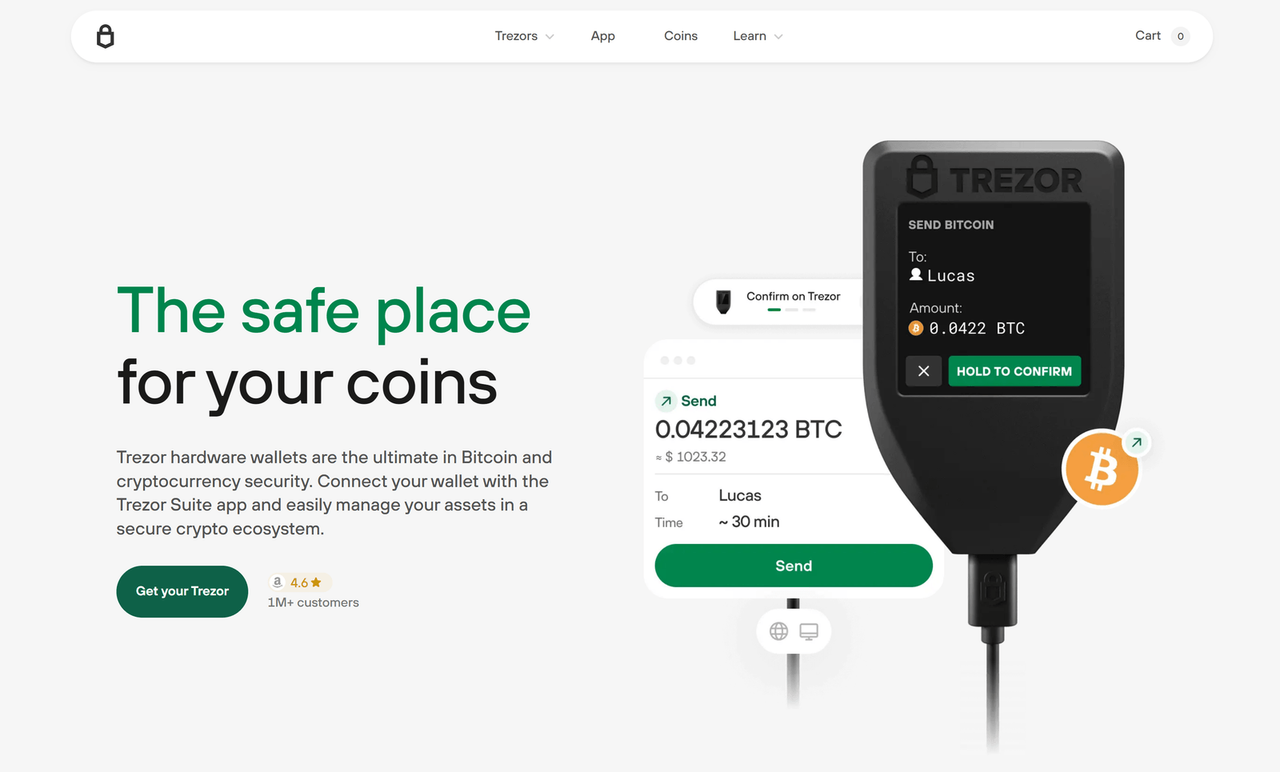
In today’s digital asset environment, where smart contracts and decentralized apps are everywhere, Trezor Login token approvals play a crucial role in protecting your crypto. If you use DeFi apps, NFT marketplaces, or any blockchain-based platform, understanding how Trezor Login token approvals function is essential. With Trezor Login token approvals, you stay in full control over what each smart contract can access in your wallet.
This detailed breakdown of Trezor Login token approvals explains how the Trezor hardware wallet ecosystem manages token permissions, how to review them safely, and how to revoke dangerous approvals.
Why Trezor Login Token Approvals Matter
Trezor Login token approvals are the backbone of secure DeFi participation. When you use DApps (decentralized applications), they request permission to access your tokens. These requests, called token approvals, can lead to major risks if not handled carefully.
Without Trezor Login token approvals, you could unknowingly authorize a malicious contract to drain your tokens. Browser-based wallets often auto-confirm or obscure what’s happening behind the scenes. That’s why using Trezor Login token approvals is a smarter and safer approach. Every permission must be confirmed physically on your Trezor device, giving you a barrier against fraud.
Final Thoughts on Trezor Login Token Approvals
Token approvals are an unavoidable part of using decentralized applications — but they don’t have to be dangerous. With Trezor Login token approvals, you gain full transparency, physical confirmation, and hardware-level protection.
From first-time users to DeFi experts, everyone can benefit from how Trezor Login token approvals enhance crypto safety. Your tokens, your control — that’s the power of Trezor Login token approvals.
If you're serious about security and ownership, there’s no better system than Trezor Login token approvals for managing smart contract permissions securely and confidently.
Made in Typedream